Latest News
September 1, 2013
It all begins with a contract, an agreement between the client and the contractor that spells out what must remain confidential during the project. “Whether we’re working with an independent inventor, an automotive and aerospace customer, or a military client, we typically start with the non-disclosure agreement (NDA),” says Tim Smith, vice president of design engineering, Altair Product Design Group.
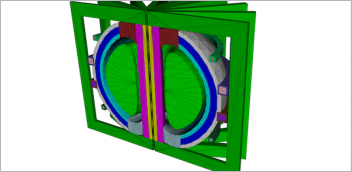
 PDX Effects’ Tommy Mueller uses GrabCAD Workbench, a cloud-hosted secure CAD file sharing service, to work on projects with his clients. They include many independent inventors and startups in need of CAD drafting and rendering services. Shown here is a digital prototype created for his client Adaptive Footwear. |
Dr. Metin Ozen, president of Ozen Engineering, concurs: “Ninety percent of the projects start with an NDA. The clients don’t show us anything until the NDA is signed.”
On one end of the spectrum are clients who, because of compliance rules and market competition, demand absolute secrecy about their projects. Aerospace and automotive titans, military institutions, and government entities fall into this category. On the other end are independent inventors and startups, with a less predictable attitude to intellectual property (IP).
Tommy Mueller, who offers 3D CAD modeling, rendering and simulation services as co-owner of the firm PDX Effects, deals with clients who belong to the latter category. He sometimes finds himself educating his clients.
“I worry about their IP,” he says. “I almost behave like a lawyer. I try to urge them not to talk to anybody. I want to make sure they’re protected. But some of them don’t know better.”
Ozen, who has also dealt with startups, observes, “Maybe the social-media type companies are more relaxed ]about IP], but not so with the companies we’re working with. They’re device makers, like biomedical equipment makers, implants makers, or semiconductor makers.” For Ozen’s startup clients, keeping the design under wraps is essential.
The clients’ insistence on a NDA might be universal, but their attitudes toward IP are hardly the same. The spectrum requires contractors and clients to negotiate the safety measures and implement what suits them best. Sometimes a trusted relationship is sufficient. Other times encryption technologies, online collaboration spaces, and working protocols augment the confidentiality. It almost always takes a combination.
What to Protect, How to Protect
Mueller, a veteran user of SolidWorks CAD software, works with many startups and independent inventors who have promising product ideas, but neither the time nor the skill to document them in 3D CAD. He relies on GrabCAD Workbench, a cloud-hosted collaboration space for sharing CAD files. With a mix of social media features, the online GrabCAD community also provides Mueller with a way to showcase his work and attract new assignments.
“Email attachments of rendered images just don’t work,” Mueller adds. “I once traded 75 emails with a client to accomplish something.” The secure co-viewing function in GrabCAD allows Mueller and his clients to review, discuss and revise design ideas online through standard browsers.
Ozen keeps his clients’ projects in an internal shared drive, cordoned off from the web. “If the customer wants a file, we actually write it on a DVD—and most of the time, hand-deliver it,” Ozen says. The firm does have an FTP site, but on extremely sensitive projects, “we don’t even use our own FTP,” Ozen says, noting that the hand-delivery policy is preferred.
Ozen’s clients usually hire the company to run simulation and finite element analysis (FEA) using ANSYS software on design ideas under consideration.
“The most sensitive documents are the reports,” says Ozen. “They contain the actual performance data of the machine or the model. They’re usually in PowerPoint, Word or PDF. The second most-sensitive are the ANSYS result files and the database, because someone who sees them sees the real design.”
Altair’s Smith notes that while some customers demand encryption for any project-related emails sent back and forth, “others limit it by saying no product data or information must pass through emails.” In many cases, Smith says, the email serves as a notice that a confidential report has been transmitted via a secure server, but the report itself is never passed along in the email. Altair’s custom IT infrastructure ensures that a report cannot be forwarded to someone else by the recipient; all intended recipients must be pre-approved so they can access the report through the embedded link.
 With its OptiStruct software, Altair Product Design group refined the cap design of Lynx brand deodorant (a Unilever product; the brand is known as Axe in the U.S.). While this project may not be top secret, the firm routinely uses OptiStruct with aerospace and automotive customers who demand strict confidentiality in consulting projects. |
Some of Altair’s military clients conduct an on-site security audit to ensure the company complies with its contractual security requirements.
“They might come and say ‘show me the server’ or ‘show me the list of users who have access to this file,’” Smith explains. “Obviously, we have to have IT that supports this type of tracking.”
When working on projects with some brand-name automakers, Altair has direct access to the client’s product lifecycle management (PLM) environment. “In those cases, the client would come and inspect our hardware to make sure it’s robust enough, and they would prescribe the type of firewalls we need to have to connect,” he explains. “We would test the data transfer, then we would get access.”
A Need-to-See Basis
The most protective companies don’t give contractors the full design—that is, the detailed assembly in CAD. “They cut it up, and give us just the part they want us to analyze,” says Ozen. “We get the design of the full device only if they want us to analyze the entire device. Like the biomedical device we’re working on right now—we need to study its torsion, bending and strength, so we do need everything.”
“With highly sensitive military clients, it’s always on a need-to-know basis,” says Altair’s Smith. “We always tell them, we need to see ]the design] in context so we understand the application and simulate it properly as it’ll work in the field.”
The partial sharing often leads to negotiations between the client and the contractors, and is also reflected in the explicit disclaimers when delivering the analysis outcome. “If the rest of the design ]withheld by the client] has some effects on elasticity, for example, we may be ignoring it,” Ozen points out. “So we put that in the report, and the client knows the limitation.”
“Invariably they give us as little as possible; invariably we point out to them, well, you have NDAs with us, so show us a little more,” says Altair’s Smith. “They don’t have to show us the rocket engine that’ll take the craft from here to Mars. But if we’re going to help them land it, we need to see at least the landing mechanism.”
IP Control is Bi-directional
In some transactions, security is a two-way street.
“We also have intellectual properties we deliver as a service provider, the methods and techniques we apply to our customer’s problem,” notes Smith. “There’s usually some negotiation that goes on with each customer.”
In many projects, Altair Product Design Group is hired to provide expertise in topology optimization—identifying the best geometric shape that satisfies the client’s requirements. Whether the project involves designing bridge trusses or airplane wing spans, Altair can deploy its OptiSruct software to explore a range of designs possible and pinpoint the best options. Impressed by the result demonstrated by Altair, the client in one such project considered applying for a patent on the resulting shape.
“We had to explain to them that they can’t patent that form because it’s not theirs. It’s intellectual property we brought to that project,” Smith recalls, noting that a client having a patent on the optimal shape “would have precluded us from offering the same solution in other projects.”
New Commerce, Evolving Security Protocols
In dealing with automotive clients, Altair also uses Trubiquity, a subscription-based encrypted file-transfer service. With one client, Smith says, Altair successfully worked on a remote CAD software program through a VPN connection—something unthinkable just five years ago because of bandwidth limitations.
“My design engineers could actually remote-control the CAD application on ]the client’s] desk,” Smith says. “Frankly, I was amazed at how responsive it was.”
This new model—the use of cloud-hosted CAD software—is being explored by software developers like Autodesk and its rivals. The shift to such a working mode is currently not commonplace, but could be in the future. If so, IP checks governing the client-contractor relationships must also evolve to keep up.
If Altair Product Design Group and Ozen Engineering represent the face of classic engineering consulting, Mueller’s PDX Effects must be the face of an emerging trend: the rise of affordable drafting, rendering and modeling service providers who cater to small, independent inventors. To these clients, freelance CAD and rendering experts like Mueller are the extended project team. They belong to the do-it-yourself (DIY) movement, fueled by personal creativity and small-scale manufacturing, producing everything from batteries with moving parts to gigantic mechanical spiders.
“We’re driving the future economy, the next manufacturing movement,” Mueller says. “Today, it only takes a group of people, not a large team, to get these ideas across.”
The advantage of a smaller team, he concludes, even if it’s kept small not by choice but by budget and operational constraints, is fewer possibilities for IP leak.
Kenneth Wong is Desktop Engineering’s resident blogger and senior editor. Email him at [email protected] or share your thoughts on this article at deskeng.com/facebook.
More Info
Subscribe to our FREE magazine, FREE email newsletters or both!
Latest News
About the Author
Kenneth Wong is Digital Engineering’s resident blogger and senior editor. Email him at [email protected] or share your thoughts on this article at digitaleng.news/facebook.
Follow DERelated Topics